Microsoft researcher Andres Freund stumbled upon a potentially catastrophic threat to Linux by chance, uncovering malicious code capable of compromising sshd authentication. This discovery, if left unnoticed, could have inflicted serious harm on Linux systems. Fortunately, the open-source community swiftly responded to this revelation, recognizing the luck in the timely detection of the backdoor. Thanks to this vigilance, the vulnerability was identified and addressed before it could escalate into a widespread issue, safeguarding the security of the broader Linux user base.
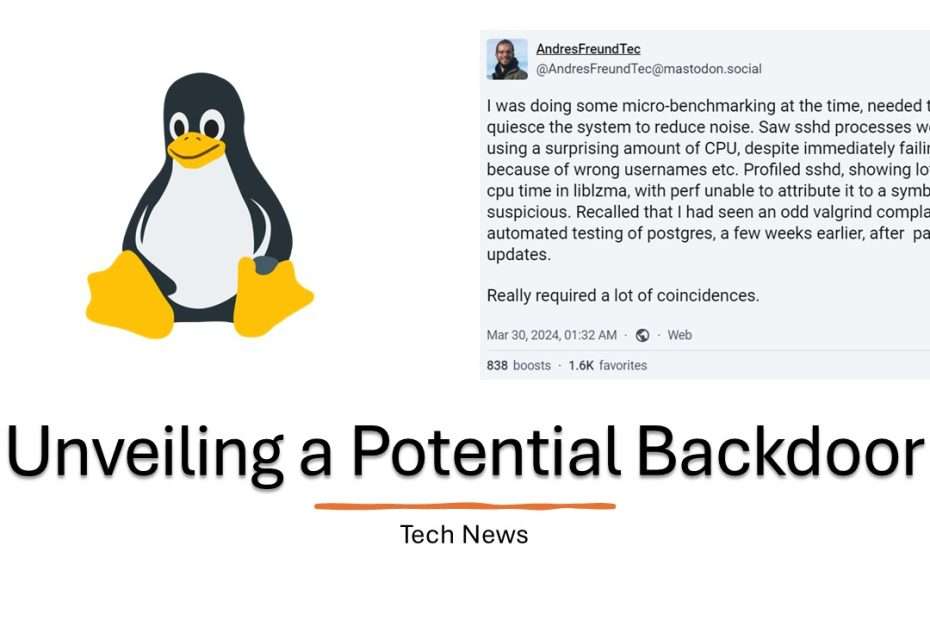
While conducting routine micro-benchmarking, Andres Freund, a PostgreSQL developer at Microsoft, made an intriguing observation. He noticed an unusual 600ms delay in ssh processes, prompting further investigation. This investigation revealed that the ssh processes were consuming an unexpected amount of CPU, contrary to what was anticipated. In his post on Mastodon, Freund shared his findings, shedding light on this unexpected behavior that caught his attention during the benchmarking process.
Following the trail of the unusual delay in ssh processes, Andres Freund’s investigation took an unexpected turn when he uncovered a supply-chain attack. Buried within the XZ package was obfuscated malicious code, indicating a potential threat to the Linux ecosystem. Freund promptly shared his discovery on the Open Source Security Mailing List, alerting the community to the presence of this insidious backdoor.
i tried explaining my nontech friends today that an engineer debugging a 500ms delay has saved the entire web, potentially the entire civilisation
— Peer Richelsen — oss/acc (@peer_rich) March 30, 2024
The attack on XZ utils, a small open-source project maintained by a single unpaid developer since 2009, has sparked a flurry of activity within the developer community. It has been revealed that the malicious code was craftily injected into the project, highlighting the vulnerability of even the most niche open-source software. The account responsible for these malicious commits appeared to have patiently gained the trust of XZ’s developer over time, suggesting a calculated and long-term approach. This discovery has led to speculation that the perpetrator behind the attack is a highly sophisticated individual or group, possibly affiliated with a nation-state agency, due to the meticulous nature of the infiltration.
The unfolding events surrounding the attack on XZ utils shed light on the challenges faced by open-source projects, particularly those with limited resources and oversight. The incident serves as a reminder of the importance of vigilance and thorough code review processes within the developer community. As the investigation continues, developers are working diligently to unravel the extent of the compromise and strengthen defenses against similar attacks in the future. This incident also underscores the critical role of transparency and collaboration within the open-source ecosystem, as developers come together to analyze, address, and learn from such security breaches.
The recently disclosed vulnerability, officially known as CVE-2024-3094, has raised significant concern within the cybersecurity community, garnering the highest possible CVSS score of 10. According to Red Hat’s report, the exploit involves the modification of functions within liblzma, a critical data compression library that forms an integral part of the XZ utils package. This library is not only essential to XZ utils but also serves as a foundational component of numerous major Linux distributions, magnifying the potential impact of the vulnerability.
With the exploitation of functions within liblzma, the CVE-2024-3094 vulnerability poses a grave threat to the security and stability of affected Linux systems. The widespread use of this data compression library across various Linux distributions means that a successful attack could have far-reaching consequences. Security experts and Linux developers are now working diligently to provide patches and updates to mitigate this vulnerability and safeguard systems against potential exploitation. Users and administrators are advised to stay informed about security updates from their respective Linux distribution providers and apply patches promptly to protect their systems from potential risks associated with CVE-2024-3094.
There was some serious time and dedication put into this attack, honestly. Talk about playing the long game https://t.co/0IZFrDAbbQ
— Ian Coldwater 📦💥 (@IanColdwater) March 29, 2024
The modified code within liblzma, once triggered, could be utilized by any software linked to the XZ library. This modification enables the interception and manipulation of data processed through the library, potentially leading to severe security breaches. Freund highlighted that under specific circumstances, this backdoor could compromise sshd authentication, providing unauthorized access to the affected system.
Moreover, Freund’s findings identified that XZ utils versions 5.6.0 and 5.6.1 are particularly susceptible to this vulnerability. Users relying on these versions are urged to take immediate action to mitigate the risk of exploitation. Given the critical role of the XZ library in numerous Linux distributions, the impact of this vulnerability could be significant. Security patches and updates are being swiftly developed to address this issue, and users are strongly advised to update their XZ utils installations to patched versions as soon as they become available.
The xz backdoor is, well, setting a fire under the entire Linux ecosystem… but I'm also so impressed with how it was set up: 2-yr maintainership, oss-fuzz, etc.
— Danny Lin (@kdrag0n) March 30, 2024
…and who knows how long it would've stayed undetected if the injected sshd code ran faster (<600ms)
Highlights:
Red Hat’s assessment of the vulnerability has led to identification of affected packages in Fedora 41 and Fedora Rawhide. As a precautionary measure, users of these versions are advised to refrain from using them until an official update becomes available. However, Red Hat Enterprise Linux (RHEL) users can rest assured as the enterprise distribution remains unaffected by this particular exploit.
Meanwhile, SUSE has taken swift action by releasing updates for openSUSE distributions such as Tumbleweed and MicroOS, ensuring users are protected against potential risks associated with the compromised XZ utils package. On the Debian Linux front, stable versions are confirmed to be safe from this vulnerability, but users of testing, unstable, and experimental versions are urged to update their xz-utils to mitigate any potential risks. Specifically for Kali Linux users, those who updated their systems between March 26 and March 29 are advised to perform another update to install the fix for this vulnerability. Users who updated before March 26 are not impacted and can continue using their systems without concern.
The evolving nature of the XZ utils vulnerability has left security researchers vigilant for potential further discoveries. Given the complexity of the situation, there is uncertainty regarding the intended payload of the malicious code. In light of these concerns, the US Cybersecurity and Infrastructure Security Agency (CISA) has recommended a cautious approach, advising users to downgrade to XZ utils versions earlier than 5.6.0, which are presumed to be uncompromised.
Furthermore, security firms are emphasizing the importance of proactive measures. Developers and users are urged to conduct incident response tests to ascertain if their systems have been impacted by this vulnerability. If any compromise is detected, it is strongly advised to report it promptly to CISA for further investigation and mitigation. This collaborative effort between security experts and users aims to minimize the potential risks associated with the XZ utils backdoor and safeguard the integrity of Linux systems.
This is explains how the xz backdoor was found pic.twitter.com/n9rNjvawHU
— myq (@mippl3) March 30, 2024
Thankfully, it has been determined that the affected versions of XZ utils were not integrated into any production releases of major Linux distributions. This assurance comes as a relief amidst the gravity of the situation. Will Dormann, a senior vulnerability analyst at security firm Analygence, emphasized the significance of this discovery, describing it as a narrow escape from potential catastrophe. Speaking to Ars Technica, Dormann remarked, “Had it not been discovered, it would have been catastrophic to the world”.
The proactive identification and response to this vulnerability underscore the importance of robust cybersecurity practices within the open-source community. The collaborative efforts of researchers, developers, and security analysts have averted a potentially devastating scenario. As the investigation continues and mitigation measures are implemented, it serves as a reminder of the vigilance needed to safeguard against such threats. The incident also highlights the critical role of timely detection and disclosure in mitigating risks to the broader technology ecosystem.
Maybe you liked other interesting articles?